12 Types of Fraud and Abuse that Everyone Should Know About
Published:
With constant changes in how we interact with external environment (e.g. how we shop, what media channels we consume, how we do banking, how we order food etc.), the types of fraud, scams and abuses are also emerging. People with malicious intent are always on the lookout for finding loopholes in systems and using those loopholes for personal gain.
In this article, I discuss about a few types of common fraudulent, abusive and other malicious activities that individuals and organizations experience. I should mention that this is a small list of types of malicious activities that exist and by the time you read this article, new type of online malicious activities might emerge. But I think, it can give a good overview of existing online risks.
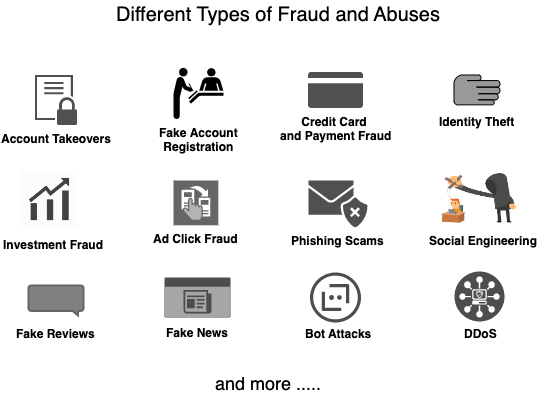
- 1. Account Takeovers:
- 2. Fake Account Registration:
- 3. Credit Card and Payment Fraud:
- 4. Identity Theft:
- 5. Investment Fraud:
- 6. Ad Click Fraud:
- 7. Phishing Scams:
- 8. Social Engineering:
- 9. Fake Reviews:
- 10. Fake News:
- 11. Bot Attacks:
- 12. Distributed denial of service (DDoS)
- Takeaways
1. Account Takeovers:
We visit many websites every day, such as Outlook, Gmail, Instagram, Robinhood, Reddit, Twitter, Amazon, Youtube and Netflix. Each website requires a username and password that stores our identity, personal data and sometimes our credit card information. However, these credentials can be hacked by someone with malicious intent through various methods like phishing, social engineering or malware installation. This is especially risky if we do not follow safe login practices like not using 2-factor authentication. Then the hacker can take over our account and perform harmful activities. For example, they could order products from Amazon using the credit card associated with our Amazon account or message our friends on Instagram asking for money. This type of risk is real and has a large-scale impact. Let me show you an example of account takeover that happened in 2020.
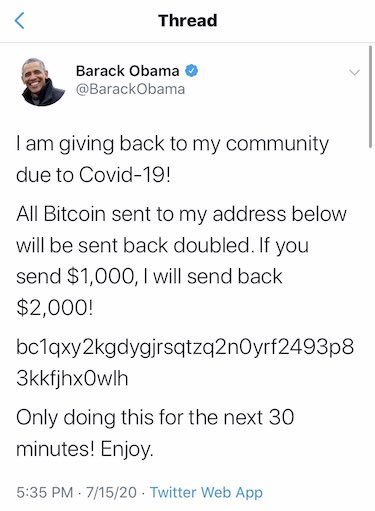
In July 2020, about 130 high-profile Twitter accounts were compromised by outside parties who used Twitter’s administrative tools to promote a bitcoin scam. They posted messages claiming that if you sent money in bitcoin to an account, it would be doubled. Within minutes of posting these messages, about $100,000 worth of bitcoin was transferred to this wallet from the victims. (wiki reference)
We may think password hacking is hard, but it’s really not. And we often make it easier for hackers. According to a Google Study from 2019, 24% of Americans have used some variation of these weak passwords: Abc123, Password, 123456, Iloveyou, 111111, Qwerty, Admin and Welcome. And 59% of U.S. adults have incorporated a name or a birthday into their password for an online account.
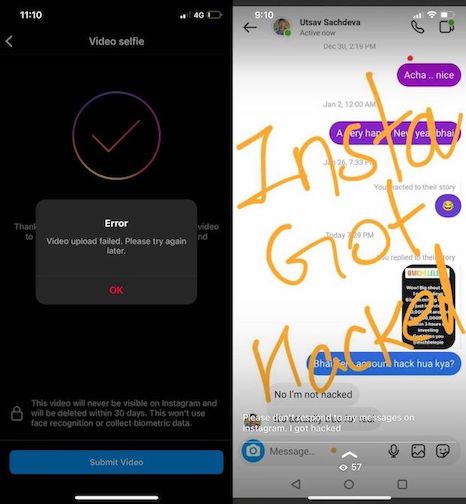
I know an account compromise incident that happened to my friend Utsav Sachdeva. His Instagram account got hacked and the attacker started posting about Bitcoin mining and asking people to follow a fraudulent account. The funny thing was that he couldn’t get back his access for a long time because of a bad password recovery workflow on Instagram. He kept getting errors in the recovery step.
2. Fake Account Registration:
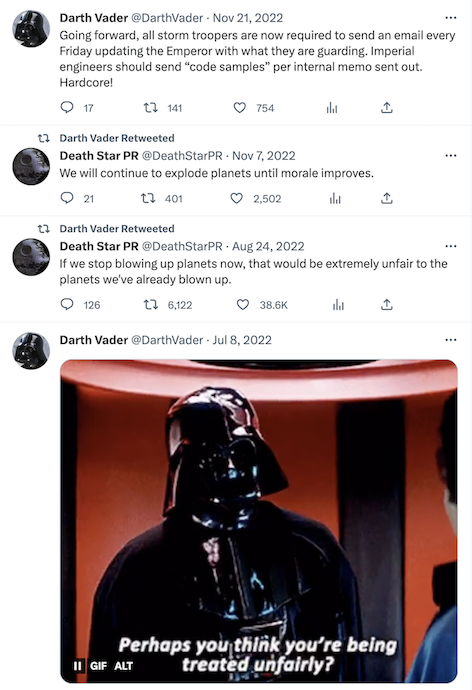
Some fake parody accounts are harmless and fun. For example, here is a snapshot of activity from the fake/parody account of @DarthVader, the Star Wars fictional character on Twitter.
But not all fake accounts are harmless or fun. Many fake accounts have malicious intent. For instance, in November 2022, shortly after Twitter started rolling out verified ticks to all paid users, a fake tweet from an impersonating account costed Eli Lilly, an American pharmaceutical company, millions of dollars. The fake account that looked like Eli Lilly’s official account posted that they were going to give insulin for free, which is their biggest revenue generator. This fake tweet led to a quick plunge in their stock price. The fake accounts are even more harmful when created by automated bots at a large scale. With computerized bots, one can create multiple fake accounts and post many social media messages. Even if one fake message gets viral, it can have a huge negative impact.

The negative impact of fake accounts is not just limited to social media platforms. The problem of fake account creation affects most (if not all) online platforms like websites or apps. Some more examples are:
- Dating platform ICONY, which is based in Germany, struggles with fake users and scammers.
- Cloud services like Amazon Web Services (AWS) struggle with stopping fake accounts from using compute services with stolen or default.
- Recently JPMorgan Chase was duped into acquiring a startup called Frank that had an enormous list of fake users.
- Companies that offer promotions to new customer accounts see bots and spam accounts misusing promotions by creating fake accounts at a large scale. In 2022, PayPal admitted having 45 million illegitimate accounts.
- Fake accounts are the first step to posting fake reviews, which we will discuss more shortly.
- Payment fraud also often starts with fake accounts, which we will also discuss shortly.
The fake accounts exist even if the platform owners enforce limits on the number of accounts a person can create. How well a platform can prevent fake accounts from happening really depends on how the limits are enforced, not just whether they are enforced or not. Does the platform block multiple accounts from the same device? How does it identify if registrations are happening from a common device? Does it use IP address or request headers like Useragent? Does it block based on the same email address? Or does it have a stronger system in place?
The problem of fake accounts also exists in the offline world. An example that we all heard a lot in 2020 was during the U.S elections when then-President Donald Trump refused to concede and made disproven claims of widespread voter fraud (wiki reference).. Even though election security officials found that the election was secure and the claims were baseless after rounds of validations, it did bring up attention to the possibility of fake registrations of voters, either with fictional names or using someone else’s names. If security systems to prevent such scenarios are not in-place, it can have a very negative impact on the trust worthiness of elections.
3. Credit Card and Payment Fraud:
There are different ways your credit card and payment information can get stolen:
1. Phishing: Phishing is using a fake website or email to trick people into providing their financial information (more on phishing will be discussed later in this article).
2. Skimming: Skimming is illegally capturing the card details including PIN by installing a data capturing device inside an ATM or card swiping machine.
3. Malware: Malware can be hidden behind a benign looking link. Once malware is downloaded and installed on someone’s device, it can copy device data or capture user activity like keystrokes.
4. Public wifi: Similar to malware, connecting to non-password protected wifi can give access to a bad actor to copy device data or capture user activity.
5. Data breaches: Large scale data breaches like breaking into an organization’s database can lead to payment and identity data leak of millions of people that can be later traded on the dark web. One of the most recent financial breaches led to a leak of data for 100 million credit card holders from Capital One bank.
Once payment information is stolen, there are different ways the fraudster might try to use the stolen information to perform transactions:
1. Card not present fraud: This is when someone uses your credit card number, expiration date, and security code to make online, phone, or mail orders without having the physical card.
2. Card present fraud: This is when someone uses a counterfeit, cloned, or altered card that looks like yours to make purchases at a store or ATM.
3. New account fraud: This is when someone first obtains your personal information, then uses it to open a new credit card under your name, and makes transactions from that card.
Many of the fraud types discussed in this article, such as account takeover, identity theft, social engineering and phishing, ultimately lead to some form of payments fraud. The main motive of the fraudsters is to make money illegally. However, the victims of stolen card details can get their money back by filing a complaint with their card issuer if they find out that their payment details are used in unauthorized transactions. In the U.S., the merchant who sells a product or service during a fraudulent transaction has to bear the cost of the chargeback. A chargeback is a reversal of a payment initiated by the card issuer on behalf of the cardholder. The U.S. consumer and card network laws protect cardholders from fraudulent transactions by holding merchants accountable for preventing them. This puts pressure on large organizations that sell products and services to make their systems secure against payments fraud. A merchant having a high percentage of chargebacks does not just lose money but also loses customer trust.
4. Identity Theft:
An individual’s privacy is the most fundamental human right. But our privacy is not protected by default. We have to take certain precautions in order to make sure our privacy and our identity stay protected. Many of our personal details can be tracked as we make phone calls, as we send texts or emails, as we post on social media or even as we go to the internet to open a website. I am not talking about cookie-based tracking. EU cookie law provides some level of protection against allowing a website to track our personal information like IP address or other activities on the browser. Quoting from The Art of Invisibility, the author shares stories on how easy it is for someone with the level of access that private investigators have to hack someone’s Social Security Number, city of birth, and even mother’s maiden name - the details that can easily be used by an impersonator to open a credit card in your name. The real person would only know that their identity is stolen when the card companies come at home asking for defaulted payments. Other common ways employed by identity thieves are social engineering and phishing. Let me give you an example of social engineering that can lead someone to steal your identity:
A Texas prison guard, Cedric, learned that he had become a victim of identity theft when he received a call from Kay’s Jewelers’ fraud unit in June 2007 telling him that someone was attempting to open an account in his name at a Kay’s Jeweler store in Austin. The company refused to open the account when they realized the person was an ID thief. Cedric checked his credit bureau report the following month and found that other creditors had run a credit check on him in June. Cedric called Sam’s Club and the two jewelry companies and learned that someone had opened credit accounts in his name. He said an ID thief charged 1,200 dollars on one card, 3,700 dollars on another account. Cedric said he filed a complaint about the ID theft with police and placed a fraud alert on his credit bureau accounts. Cedric said police believe his personal information was stolen from a dealership where he purchased a vehicle. (reference)
Once identity thieves have access to your personal information, they can harm you in a bunch of ways. These can be:
- Open a new credit card account. When they don’t pay the bills, the delinquent account is reported on your credit report.
- Open a phone number or internet connection in your name and use it for free.
- Create a social media profile with your identity and perform harmful or abusive activities impersonating you.
- Get your health insurance
- etc.
When and where your information is at risk to be stolen?:
- Wherever you fill forms online or offline, when you buy something like a car or insurance, when you register for a new account online or offline, you are prone to get your identity stolen.
- When you use public Wi-Fi networks or computers that may have malware or spyware installed, hackers can access your personal information and use it for fraudulent purposes.
- When you lose your wallet, purse, phone or other devices that contain your personal information, identity thieves can find them and use them to open new accounts or make purchases in your name.
- When you receive unsolicited calls, emails or texts that ask for your personal information, such as your Social Security number, bank account number or credit card number. These are often phishing scams that try to trick you into revealing your information by pretending to be a legitimate company or organization.
- When you discard documents that contain your personal information without shredding them first. Identity thieves can go through your trash and find these documents and use them to steal your identity. (reference)
5. Investment Fraud:
Investment fraud is a type of fraud where someone misleads investors for personal gain. Ponzi schemes, pyramid schemes, pump and dump schemes, and insider trading are some of the different ways investment fraud can be committed in the market.
It’s Feb 2023, and FTX recently collapsed on November 11, 2022. I have to talk about FTX in this section as FTX is one of the biggest financial frauds in American history and is related to investment fraud. Sam Bankman-Fried, founder of FTX, misled customers about the risks and returns of investing in crypto through his platform. The ripple effects of the collapse were huge with a sharp crash of Bitcoin and other major cryptocurrencies. As of today, the market is still suffering from those effects with multiple other crypto platforms including BlockFi and Genesis going bankrupt.

The image is from an FTX ad. I just want to show how big FTX had become that celebrities including Larry David (from the picture), Tom Brady, Gisele Bündchen, Stephen Curry made an FTX commercial.
Another common way to commit investment fraud is pump and dump scheme. One pump and dump scheme (it is debatable whether it is a fraud or not) is from early 2021 with GameStop, Blackberry, and AMC stocks. These stocks were hyped up by online forums on Reddit like Wall Street Bets, causing a surge in demand and price. However, many investors lost money when the prices plummeted after the hype faded. A Ponzi or pyramid scheme is a form of fraud that lures investors and pays profits to earlier investors with funds from more recent investors. It is named after Charles Ponzi (died 1949), who carried out such a fraud (1919–203). One example of a Ponzi scheme is Bernie Madoff’s investment firm, which defrauded thousands of clients of billions of dollars over decades.
6. Ad Click Fraud:
In this section, I will discuss about two types of fraud around online ads. First one is click fraud, in which people click on ads without a genuine interest in the product or service behind the ad. Fraudulent clicks can be done by softwares or by humans. The purpose of click fraud is either to increase the revenue of a website hosting ads or deplete the budget of an advertiser who pays for each click. The second is malvertising, in which fraudsters embed malware to legitimate looking ads. Ads on legitimate platforms get a lot of clicks making it a lucrative option for malicious malware developers to hide malicious code behing the ads. On clicking such ads, user’s devices get infected with malware that can steal personal data and hijack the device resouces. In 2017, Google took down 79 million ads that attempted to send people to malware-laden sites, 66 million “trick-to-click” ads as well as 48 million ads that were attempting to get users to install unwanted software.
7. Phishing Scams:
Phishing is a cybercrime that involves sending fake emails, messages or voice calls to trick people into doing something that they otherwise wouldn’t do. Most commonly, in phishing emails or messages, people are tricked to click a link that takes them to a website that mimics an official website of a well known company and asks them to provide account details. For example, you would believe that you received an email from your bank. Then you will be prompted to provide a username and password on a portal that looks just like real company, but its actually fake. The data you provide in the portal directly goes in the hands of fraudster. In many cases, people use same username-password in multiple accounts giving fraudster an access to multiple of your accounts.
In a similar manner, people can be tricked to share payment details like credit card numbers, license keys, download some attachment that can install malware in your device,
One of the largest phishing scams targeted Google and Facebook (yes, the two large tech giants), and successfully made the companies to transfer a total of $100 million to scammer’s bank accounts. To carry out the scam, Rimasauskas (the scammer) sent emails to employees who used to handle large transactions in the two tech giants. In the emails, he impersonated Quanta Computer, a Taiwan-based company that actually does business with both Google and Facebook. The emails and fake invoices he forged asking for payment were so real that even business executives of big companies were duped to complete the transactions. He was later caught, pleaded guilty, and now serves time in U.S prison. But the incident surfaces the level at which phishing scams can harm the society.
Phishing is also connected with other types of fraud discussed above. For example, phishing could be a first step leading to an account takeover, identity theft and payment fraud. Phishing is also considered as type of social engineering as it involves manipulating human psychology. You might also hear about “spear phishing attacks”. These are phishing attacks that are targeted to a specific individual or organization. The attack on Google and Facebook is an example of spear phishing attack. Then there is “Whaling” in which the attackers target high profile people. One of the biggest instances of Whaling was Celebgate, 2014 in which the attackers gained illegimiate access to personal pictures of various celebrities from their iCloud accounts via phishing.
Let me show some examples of phishing messages that I personally received:
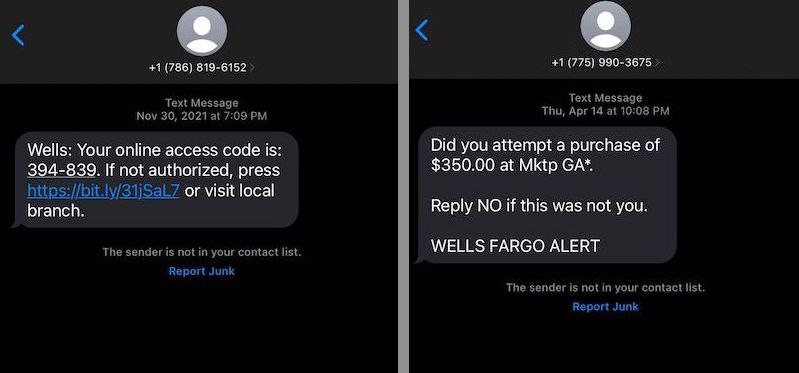
The above messages look like they are sent from Wells Fargo bank, where I happen to have an account in the past. Some of the things to note here and are common in most of the phishing emails or messages are:
- The provided link is either short url or has misspelled company name,
- You are asked to take an action like clicking a link or sending a message,
- Once you click the link (which by the way you shouldn’t), it would take you to a portal that looks justs like Wells Fargo, asking your to login. Once you do that, your username and password will go to fraudster and first thing they might do is change the password in your real account or try to make some transaction from your account.
8. Social Engineering:
Social engeering is deceving people into revealing personal or confidential information that can be used for all the fradulent practices discussed in this article. Phishing, that we just discussed in the previous section is a type of social engineering. But there are other ways too that fraudsters can use to trick people into revealing information. Let’s discuss some of the other ways:
Baiting: Baiting is enticing others to reveal some personal information by offering something good. Offering free discounts, offering a lucrative job, offering free software updates, offering a gift card etc. are different baits that can make someone to reveal a personal information. With laying out simple baits, people can reveal their email address, phone number, physical address, or in the worst case social security number. Social engineering scams are also often targeted towards the victim’s area of interst. What seems lucrative to one person might not be lucrative to another. For example, someone working in a startup as a software engineer would not even reply to a recruiter from Shell Oil for a job opportunity in an oil rig. But the same person might feel enticed if receives an email from a recruiter at Google for a software engineering job, asking to share resume. Then the scamming recruiter might ask for a full physical address to continue with application. Revealing a full physical address can consequently make it easier for them to hack into someone’s income tax accounts as the address is often used as security question by the income tax department. Anything that is free or lucrative is questionable for a possible social engineering scam.
Fake Alerts: Fake alerts or warnings can scare you to act urgently that you might not even get a chance to think rationally or realize that you are being scammed. Examples are fake warning about your bank account being hacked, or that your device is infected by malware. I once received fake warning call from someone impersonalting police, that my identity is used to register for credit cards and those cards are being used to make drug payments. After 3 minutes on the call (yes took some time), I realized that it was a scam to make me reveal the information that would indeed lead to a true identity theft. But I did feel the sense of urgency and fear, as would have been the intention of the scammer. On checking with credit bureau, I found no malicious activity, but still froze my credit file for a while. Scammers often impersonate someone with public authority or someone you know, like a family member or a friend to escalate the sense of fear and urgency.
Quid pro quo: “Favor for a favor”. The most famous Quid pro quo scam is Nigerian Letter Scam, also known as advance fee fraud or “419 fraud”. It’s a scheme in which a sender requests help in facilitating a transfer of large sum of money for a “self-proclaimed government entity” in return for a sizable commission that one helping would receive. It was widespread during 1990 and commonly the self-proclaimed entity and was originated in Nigeria (the 419 code is the Nigerian Criminal Code). Many people received the request via mail, fax or email in which they were offerred a large commission (sometimes 10 million dollars) for helping the transfer. In order to initiate the process, they were then asked to follow some process and pay small notary fees, somewhere like $50 (or more depending on the gullability of the victim). Scammers ofcourse just wanted the notary fees from victims and vanished after receiving the same. Believe it or not, thousands of people fell for it.
Today, Google automatically puts many such emails in Span folder. But fraudsters constantly try to find new ways.

An email sample on the lines of Nigerian letter scam.
9. Fake Reviews:
If you go to support.google.com/business, and search for fake reviews, you would find a number of threads that are created by business owners seeking help from Google about possible fake reviews posted on Google about their services. I did the same and one thread stood out to me. In that thread, the business owner raised the complaint and provided screenshots of reviews that they thought to be fake and provided reasons on why they thought the specific reviews were fake. Here is one of the example of fake reviews business provided to Google, that was later taken down:
The user: “Really so bad experience”.
Business: “As we haven’t ever worked together or met, I just wanted to reach out and see what has prompted”
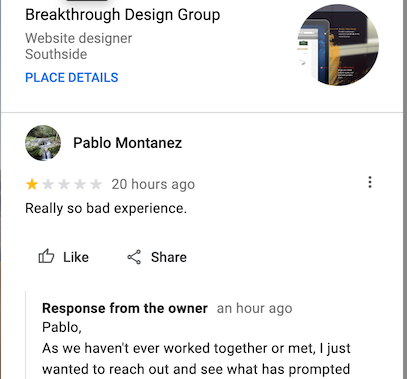
In the complaint, the reviewer talked about a bad experience with the business, but the business claimed that they never worked with the customer who wrote the review. Situations like these become about the word of business against word of reviewer, and are challenging for review platforms (like Google, Yelp, Amazon etc.) to differentiate fake reviews from the legitimate ones. But certain common patterns do exist in fake reviews including,
- Similar reviews getting posted in short intervals from multiple accounts, each account having no past activity,
- Generic reviews that could be applicable to any business,
- The business having never worked with specific reviewer,
- Reviews from stolen identity or stolen photo of another person on the internet, etc.
Fake or false reviews can be either positive or negative. They are meant to either pump up or hurt the online rating of a product, service or a business. Negative fake reviews can be written by competitors, ex-employees, trolls or third-parties with a grudge against businesses. And the positive reviews are organized by business owners themselves to falsely promote their product or sercives. Whether the reviews are negative or whether they are, the customers are deceived and the businesses can be hurt.
10. Fake News:
Fake news is presenting a misleading or fake information as news or as fact. It is a serious problem today, especially post Covid-19 era. Fake news mislead people in believing something that isn’t true. As a result of believing facts that aren’t true, people can take irrational decisions and actions, harming themselves and society as a whole.
Over the last few years (2019-2023), fake news has become an everyday expression, and a major part of any discourse around the media. During this period, people claimed made up cures for the new coronavirus like eating boiled garlic or drinking bleach or inhaling stream. The consequence of believing these claims causes more harm than good and the consequences become an issue on public health, trust and democracy. Which is why, social media platforms like YouTube, Twitter, Facebook started flagging posts that claimed a false fact and were blocking accounts that posted multiple such posts.
11. Bot Attacks:
“Bot” is the term used for a software application that can perform automated tasks over the internet. The automated systems can perform a task much faster and many many times than a human can do. Bots can be both good and bad. Fraudsters use bad bots to orchestrate fraud attacks at large scale, launching thousands of attacks at the same time.
Why do fraudsters use bot? Because the success rate of fraud attacks are low. Taking an example of credential stuffing to perform an account takeover attack, a fraudster would have to try stuffing credentials in many accounts before being able to get access to a single account. Bot helps them to do the same at scale, trying out a list of credentials in many accounts at the same time. This opportunity of performing a large scale attack also makes bots a lucrative option for fraudsters to target big tech organizations.
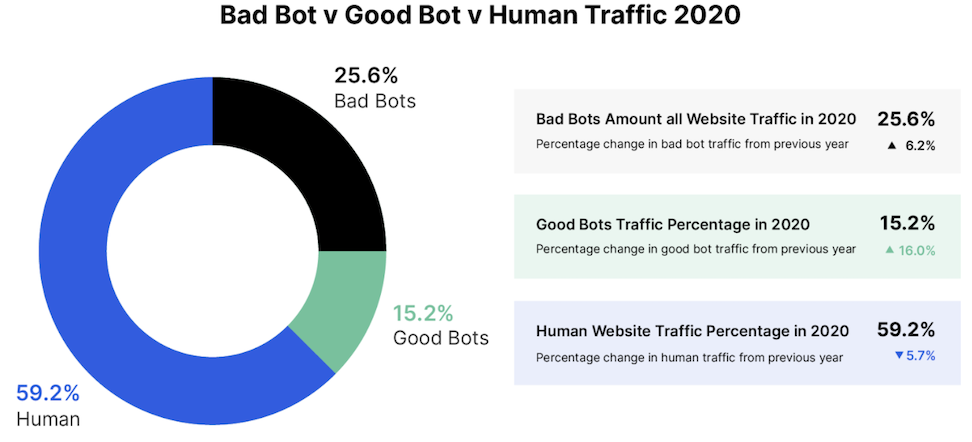
According to 8th Annual Bad Bot Report from Imperva, bad bot traffic amounted to 25.6 percent of all website traffic in 2020. To repeat, a quarter of ALL internet traffic was bot. This is huge. According to the same report, Telecom and Internet Service Provider (ISP) companies are hit largest by bot attacks. The problem of bad bots is not just that they compromise a large proportion of the internet activity, but the fact that they are not always easy to track. Advanced bots mimic human behaviors, use proxies, frequently change their IP addresses and identities making them difficult to track.
There are multiple ways bots can cause harm:
1. Account takeover: First and foremost is account takeover. Attackers use bots to try out username and password combinations for different accounts. These passwords can sometimes be bought from dark web if a data breach has recently occurred. Bots also make it easier for fraudsters to just try out many many usernames and passwords on many websites by brute force.
2. Carding: Brute force option of trying out usernames-passwords also applies to just trying out many many card numbers until one that is active and works is found.
3. Ad click fraud: Ad click fraud can also be done at large scale with bots.
4. Fake registrations: Fraudsters use bots to register a large number of accounts. Those accounts are later used to perform other bot attacks or to exploit free-trials.
5. Spamming: Fraudsters use bots to post a bunch of harmful content on social media or review platforms.
6. Competetive data mining: Competetors can use to mine price, inventory or sales data to beat you in marketplace.
4. Distributed denial of service (DDoS): Let’s just move on to next section and discuss about distributed-denial-of-service in a bit more detail.
12. Distributed denial of service (DDoS)
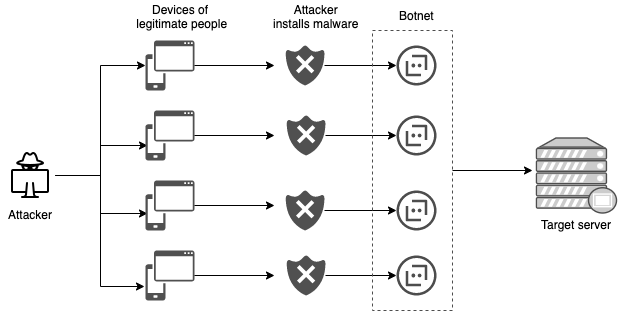
A distributed denial-of-service (DDoS) attack is a malicious attempt to disrupt the normal traffic of a targeted server, service or network by overwhelming it with a flood of internet traffic. That flood of internet traffic is often created by first installing a malware in peoples’ device (we have already learnt how attackers install malware) and taking a control of their device, and then creating a network of bots (a.k.a botnet) from now controllable devices. The network of these distrbuted devices are then used to hit servers of the final attack target. Attackers use the compromised devices of real people because doing so makes it difficult to track them down.
But, what is the attackers’ goal with DDoS? Why are they causing unnecessary traffic? Let’s say the targeted victim is Walmart.com. A DDoS attack can overload Walmart’s servers with botnet such that the regular traffic, i.e. real customers wanting to buy something from Walmart are not able to connect (denial of service). This would negatively impacting sales.
I like the following analogy from Cloudfare about DDoS: A DDoS attack is like an unexpected traffic jam clogging up the highway, preventing regular traffic from arriving at its destination.
The DDoS is one of the oldest and dynamically advancing vector of cybercrime. It was first originated in 1996 against Panix, an ISP in New York. There is a lot of cybersecurity literature diving deep into DDoS attack vectors. But my goal with this article is not to go that deep and I would conclude it here.
Takeaways
In this article, we talked about 12 different ways fraudsters can harm individuals, society and organizations. These are just a few of the common methods that fraudsters use. But with constant changes in technology, new ways to commit fraud keep emerging.
What’s interesting about fraud networks is that they are also interconnected. For example, we discussed malvertising in ad click fraud where fraudsters embed malware into legitimate-looking ads. Malvertising can be just the first step in a bigger goal for a fraudster. By installing malware, a fraudster can either try to steal identity or payment information from the victim’s device or might try to get control of devices of multiple such victims to create a botnet that can be later used for distributed denial-of-service attacks against a big organization. Many fraudsters also play a long game where they establish trust with the target either using social engineering tactics or just behaving like a legitimate human for a long time before striking.
When writing the takeaway section, I wondered if I had unintentionally scared the readers. It could be so. My goal to write this article was not to scare you but to set a context about the widespread potential of fraud in all parts of our lives. For organizations, it is crucial to have advanced fraud management solutions and employ a proactive approach against fraud detection. If an organization follows a reactive approach instead (i.e., mitigating loss from fraud after it occurs), they tend to stay busy on mitigating the damage that has already been done rather than working on strategic solutions to prevent such damages from happening in the future. Such organizations suffer from higher operational costs, more employee frustration who are constantly engaged in whacking moles (mitigating fraud damage), lower customer trust and lower customer retention. According to a survey done by Google and Forrester, two thirds of their survey respondents, are unable to do proactive threat hunting, since they are tied up in the day-to-day management of bot attacks.
If you found this article interesting, consider subscribing to my email list for more content around fraud detection.